Last updated:
 Why Trust Cryptonews
Why Trust Cryptonews

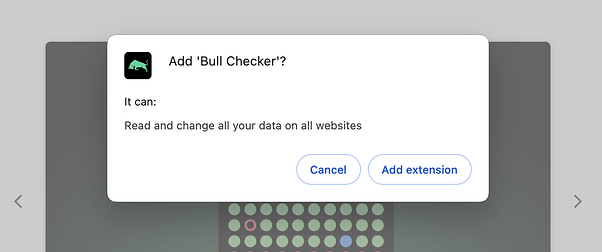
A malicious Chrome Extension dubbed “Bull Checker” has been targeting Solana DeFi users, draining their tokens in the past week.
Decentralized trading platform Jupiter Exchange first identified the browser extension, flagging that it has been stealing several Solana users’ tokens.
Jupiter conducted a detailed investigation on the chrome extension, following reports from users losing their tokens. Per the report published on Tuesday, Bull Checker was initially legitimate-looking, allowing users to interact with decentralized applications (dApps) as usual.
“Users with this extension would interact with the dApps as per normal, have the simulation show up as normal, but have the possibility of their tokens being maliciously transferred to another wallet upon transaction completion.”
After installing the extension, it would wait for the user to interact with the dApp on the official domain. It would then modify the transaction sent to the wallet to sign, Jupiter wrote.
Interestingly, the simulation result appeared to be “normal” and not appear to be a drainer even after modification.
Further, the platform confirmed that there is no vulnerability within the wallets of dApps.
The investigations revealed that Bull Checker had the permission to read and change all the data on the website.
Raydium, an automated market maker (AMM) built on the Solana blockchain, also apparently reported that their affected users had the same extension installed.
“Malicious instructions were added to regular Jupiter and Raydium instructions, and the resulting transaction was signed by the user as per normal, but had their tokens and authority transferred to the malicious address,” Jupiter wrote on X.
Bull Checker was a ‘Read-Only’ Extension
Jupiter further flagged that the malicious extension was ‘read-only,’ allowing users to “view the holders of memecoins.”
“There should be no need for an extension like this to read or write data on all websites,” it added.
However, several users continued to install and use Bull Checker, despite this potential major red flag.
Additionally, Bull Checker was publicized by an anonymous account on Reddit, targeting those who are looking to trade memecoins. The account “Solana_OG” then lured those users to download the extension.
Jupiter also listed down some of the safety measures that users have to keep in mind before installing any such extensions.