Last updated:
 Why Trust Cryptonews
Why Trust Cryptonews

Blockchain analytics firm Chainalysis has released a detailed report on Feb. 24 linking the $1.46 billion cryptocurrency heist at Bybit, a Dubai-based crypto exchange, to North Korean hackers.
The attack, which took place on Feb. 21, is the largest in crypto history and highlights the increasing sophistication of state-sponsored cybercriminals.
Chainalysis Uncovers the Attack’s Execution
According to Chainalysis, the exploit followed tactics commonly associated with the Democratic People’s Republic of Korea (DPRK).
In our latest blog, we look at how the near-$1.5 billion Bybit exploit occurred, the attackers’ link to the DPRK, and how we are collaborating with Bybit and law enforcement to help recover funds: https://t.co/MOh0JQZd9V pic.twitter.com/iIwF2xm1b0
— Chainalysis (@chainalysis) February 24, 2025
Hackers used a phishing campaign to infiltrate Bybit’s cold wallet signers, tricking them into approving malicious transactions. This allowed attackers to alter the multi-signature security setup and seize control of the funds.
Once inside the system, they intercepted what appeared to be a standard transfer from Bybit’s Ethereum cold wallet to a hot wallet. Instead, they rerouted approximately 401,000 Ether (ETH) – worth nearly $1.4 billion – to addresses under their control.
Laundering Stolen Crypto
After securing the funds, the hackers employed a complex laundering strategy.
Chainalysis reported that they moved the stolen assets through intermediary wallets, making tracking more difficult. The criminals then used decentralized exchanges (DEXs), cross-chain bridges, and no-KYC instant swap services to convert ETH into Bitcoin (BTC) and DAI, a stablecoin that lacks a freeze function.
A large portion of the stolen assets remains dormant, or inactive – a tactic often employed by North Korea-linked hackers to avoid immediate detection. By waiting for scrutiny to subside, they increase their chances of moving the funds successfully.
Industry Response to ByBit Hack
Blockchain investigators, analytics firms, crypto exchanges, and network protocols are working together to trace and recover the stolen funds.
One such effort includes the cross-chain trading protocol Chainflip, which is implementing an emergency software upgrade to prevent hackers from moving funds linked to the Bybit exploit.
On Feb. 24, Chainflip announced the “1.7.10” upgrade, designed to block illicit transactions and protect liquidity providers from exposure to stolen funds.
On Feb. 22, Bybit also pledged to cover customer losses and has launched a bounty program, offering up to 10% of the recovered amount to those who help retrieve the stolen funds.
Working with Tether, Circle, Tron and other teams, Bybit was able to freeze over $40 million in stolen assets in a single day.
A coordinated effort led to the freezing of $42.89M in just one day. Thanks to the following teams for their swift action: @Tether_to: Flagged address and froze 181K USDT @THORChain: Blocked the blacklist @ChangeNOW_io: Froze 34 ETH @FixedFloat: Froze 120K USDC + USDT…
— Bybit (@Bybit_Official) February 23, 2025
North Korea’s Expanding Crypto Attacks
Another Chainalysis report from December 2024 notes that North Korean cybercriminals have significantly escalated their crypto theft operations in recent years.
In 2023, they stole $660.5 million across 20 incidents. By 2024, that number had more than doubled, reaching $1.34 billion across 47 attacks.
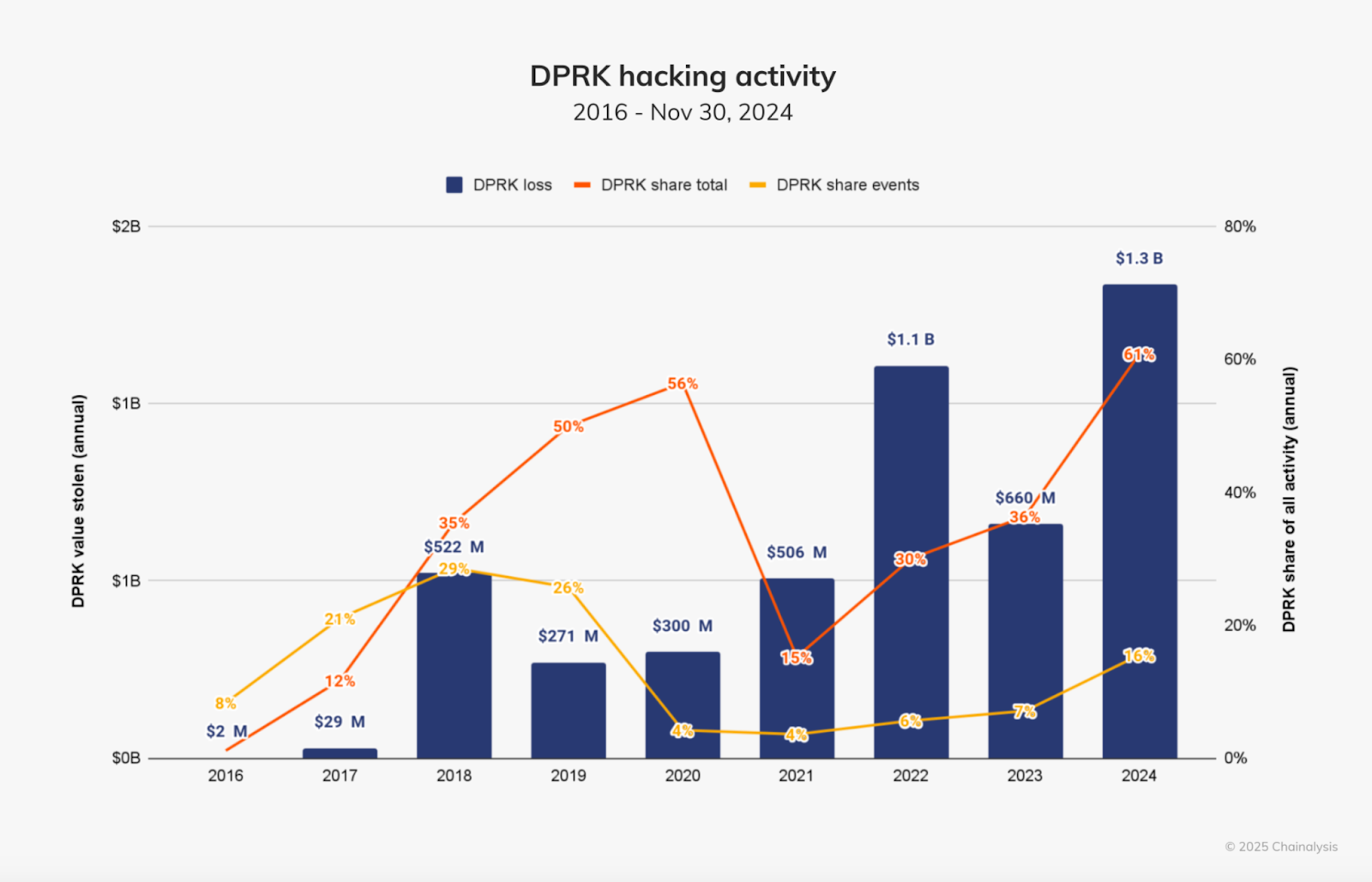
The Bybit exploit alone exceeds all funds stolen by North Korea throughout 2024, making it a landmark event in the ongoing cyber warfare linked to the regime.
According to Chainalysis, North Korea-linked hackers have built a reputation for their highly advanced and persistent cyberattacks, frequently using malware, social engineering, and cryptocurrency theft to fund state-sponsored operations.
Chainalysis has also noticed another disturbing trend: North Korean hackers are attacking crypto platforms more frequently and executing larger-scale exploits.
In 2024, attacks of all sizes became more frequent, with incidents involving thefts of over $100 million occurring far more often than in previous years. This shift suggests that the DPRK is refining its attack strategies and accelerating its operations, making its cyber threats increasingly difficult to counter.