Last updated:
 Why Trust Cryptonews
Why Trust Cryptonews

EigenLayer’s X account, the second-biggest protocol on Ethereum, was hacked on October 18 to front an airdrop scam. One victim’s wallet was drained of over $800,000 in crypto.
In an X post, EigenLayer Labs highlighted an ongoing compromise of the “@EigenLayer” account handle.
Pseudonymous on-chain investigator ZachXBT initially warned users about the malicious airdrop link, cautioning them not to interact with any links in a Telegram post.
Security analyst Scam Sniffer reported that the scam apparently fleeced at least one unsuspecting victim out of at least $800,000 in cryptocurrencies.
While no account recovery has been reportedso far, the fraudulent posts are actively being taken down.
EigenLayer Hacker Runs Airdrop Scam Campaign
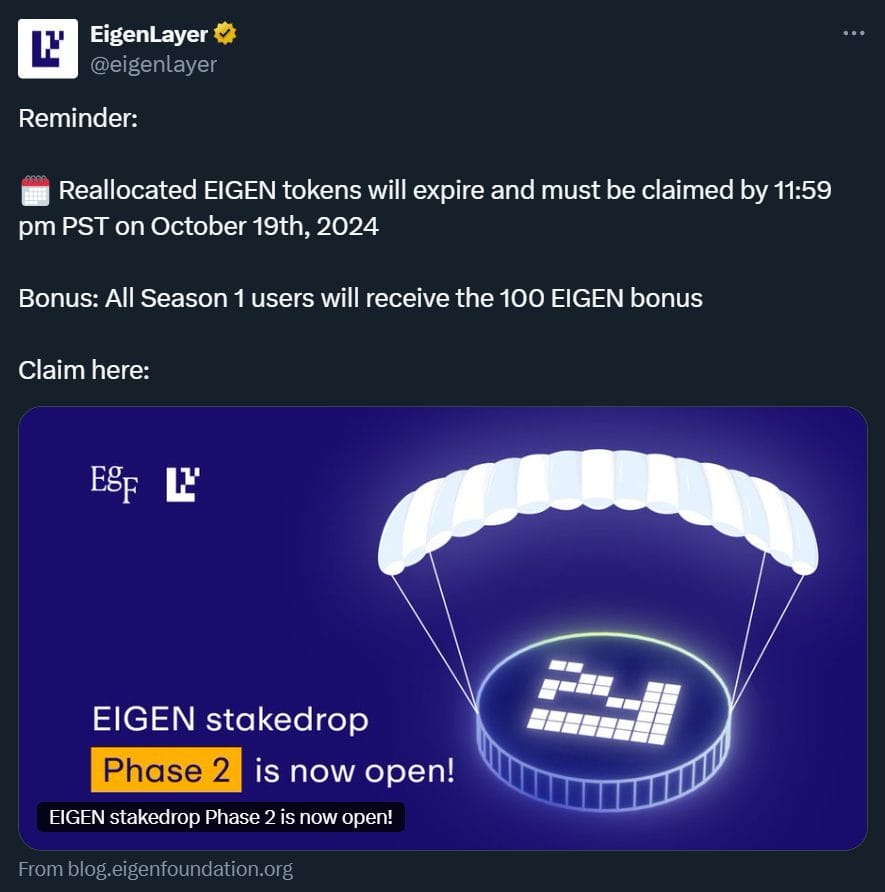
Despite intervention attempts, the account continues to post malicious links, urging users to engage with “reminders” and “final calls” for the supposed reallocation of EIGEN tokens from EigenLayer’s Season 2 airdrop.
The claim period for Season 2 of EigenLayer’s stakeholder airdrop ended last month, however.
The hacker’s X posts are almost indistinguishable from EigenLayer’s typical post format, even tying themselves into threads containing fake EigenLayer blog entries to mask the scheme.
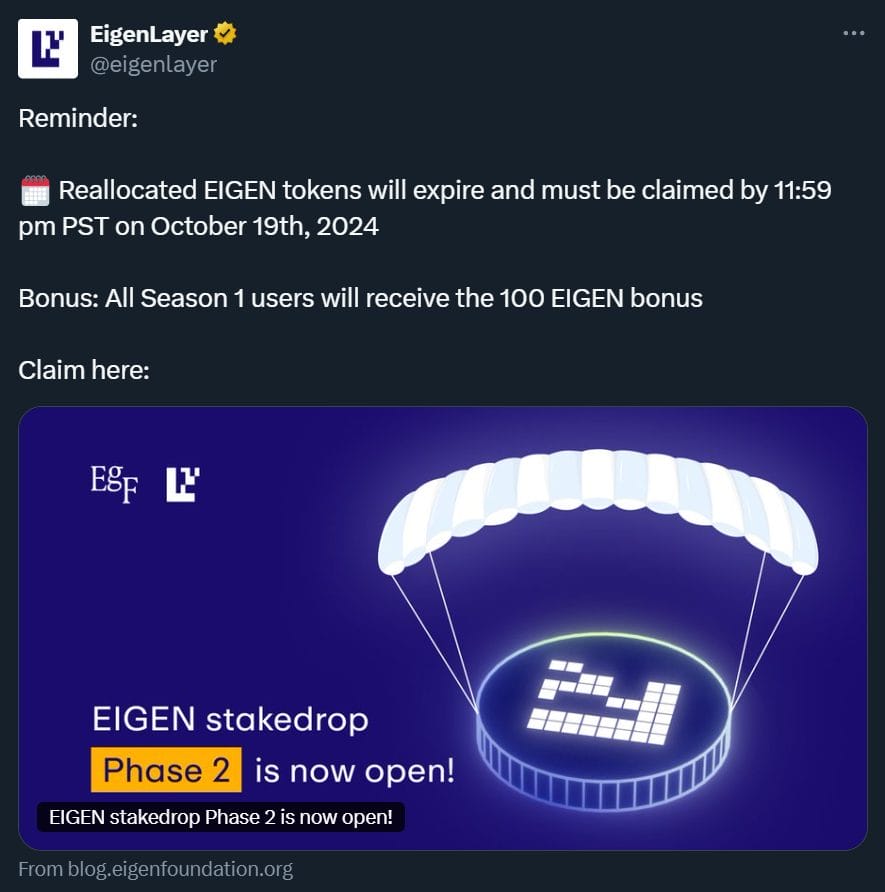
However, ZachXBT noted a key differentiator: EigenLayer’s official blog URL is “blog.eigenlayer.xyz,” whereas the malicious link redirects users to “blog.eigenfoundation.org.”
Upon arrival, the scam site prompts users to enter the supposed airdrop and connect their wallet address to “claim EIGEN.”
This is a common tactic among scammers: tricking users into handing over account access to run a wallet drainer scam, which cleans any connected wallets of their cryptocurrencies.
Exploring further, users can navigate a close recreation of the EigenLayer website and various blog posts, all funneling back to the airdrop scam in an elaborate rouse.
EigenLayer has advised users to be cautious and double-check URLs, noting that they would provide further updates once the account is secured.
In the cryptocurrency industry, hacking verified social media accounts to promote fraudulent websites or scam coins is a common practice. It’s crucial to stay vigilant against such attacks.
EigenLayer Becomes Prime Scam Target
This attack adds to what seems to be a pattern as EigenLayer becomes a ripe target for scammers, marking the second compromise since the beginning of October.
In an October 4 X post, the EigenLayer team highlighted an investigation concerning “unapproved selling activity” from a wallet address. The address in question sold about 1.6 million $EIGEN tokens, worth approximately $5.7 million.
The following day, EigenLayer posted a community update crediting the incident to a hack. They revealed that a malicious attacker compromised an email thread involving an investor’s token transfer into custody.
While tokens were stolen through a hack, the EigenLayer team assured the community that the hack was an “isolated” incident and did not affect its broader ecosystem.
They emphasized that the compromise was unrelated to any on-chain functionality and added that there is no known vulnerability in the protocol or token contracts.